About CyberArk Software
CyberArk Software Ltd. (CyberArk) operates as a global leader in identity security, centered on intelligent privilege controls, with a focus on protecting organizations against identity-based cyberattacks.

In July 2022, the company acquired C3M, LLC, a provider of multi-cloud security and compliance solutions.
The company applies intelligent privilege controls to all identities – human & machine – with continuous threat detection and prevention across the entire identity lifecycle. With CyberArk, organizations can enable Zero Trust and least privilege with complete visibility, ensuring that every identity can securely access any approved resource, located anywhere, from everywhere – with a single Identity Security Platform.
As of December 31, 2022, the company had more than 8,000 customers, including more than 55% of Fortune 500 companies and more than 35% of Global 2000 companies. The company’s customers include leading organizations in a diverse set of industries, including financial services, manufacturing, insurance, healthcare, energy and utilities, transportation, retail, technology, and telecommunications, as well as federal and local government agencies in multiple countries. The company sells its solutions through a high-touch hybrid model that includes direct sales, channel sales, managed security service providers, and advisory firm partners.
Growth Strategy
The key elements of the company’s long-term growth strategy include strengthening the company’s Identity Security leadership position by delivering ongoing innovation; extending the company’s global go-to-market reach; growing the company’s customer base; expanding its relationships with existing customers; and driving strong adoption of its solutions and retaining the company’s customer base.

Solutions
The company’s Identity Security Platform provides a complete and flexible set of Identity Security capabilities across six main solution areas: Workforce and Customer Access, Endpoint Privilege Security, Privileged Access Management, Secrets Management, Cloud Privilege Security, and Identity Management.
Privileged Access Management
CyberArk’s Privileged Access Management solutions can be used to secure, manage, and monitor privileged access. Privileged accounts can be found on endpoints, in applications, and from hybrid to multi-cloud environments.
Privileged Access Manager: CyberArk Privileged Access Manager and CyberArk Privilege Cloud include risk-based credential security and session management to protect against attacks involving privileged access. CyberArk’s self-hosted Privileged Access Manager solution can be deployed in a self-hosted data center or in a hybrid cloud or a public cloud environment. CyberArk Privileged Cloud is a SaaS solution.
Vendor Privileged Access Manager: CyberArk Vendor Privileged Access Manager combines Privileged Access Manager or Privilege Cloud and Remote Access, a SaaS solution, to provide fast, easy and secure privileged access to third-party vendors who need access to critical internal systems via CyberArk, without the need to use passwords. By not requiring VPNs or agents, Vendor Privileged Access Manager removes operational overhead for administrators, makes it easier and quicker to deploy and improves organizational security.
Dynamic Privileged Access: CyberArk Dynamic Privileged Access is a SaaS solution that provisions just-in-time (JIT), privileged access to Linux Virtual Machines (VMs hosted in AWS and Azure and on-premises windows servers). The solution leverages attribute-based access control (ABAC) and full session isolation to drive measurable risk reduction. Dynamic Privileged Access allows organizations to unify controls for JIT and standing privileged access across public cloud and on-premises systems, enabling operational efficiencies while progressing towards Zero Standing Privileges (ZSP) and Zero Trust initiatives.
Endpoint Privilege Security
Endpoint Privilege Manager: CyberArk Endpoint Privilege Manager is a SaaS solution that secures privileges on the endpoint (Windows servers, Windows desktops and Mac desktops) and helps contain attacks early in their lifecycle. It enables revocation of local administrator rights, while minimizing impact on user productivity, by seamlessly elevating privileges for authorized applications or tasks. Application control, with automatic policy creation, allows organizations to prevent malicious applications from executing, and runs unknown applications in a restricted mode. This, combined with credential theft protection, helps prevent malware, such as ransomware from gaining a foothold and contains attacks on the endpoint.
Secure Desktop: CyberArk Secure Desktop solution lets businesses protect access to endpoints and enforce the principle of least privilege without complicating IT operations or hindering user productivity. The unified endpoint multifactor authentication and privilege management solution helps organizations strengthen access security, optimize user experiences, and eliminate the manually intensive, error-prone administrative processes that can lead to over provisioning and privilege abuse.
Workforce & Customer Access
The company deliver robust Identity as a Service (IDaaS) which provides a comprehensive Artificial Intelligence (AI)-based and security-first approach to managing identities that is both adaptive and context-aware. CyberArk Identity includes capabilities to secure both workforce and customer identities.
Workforce Identity offers:
Adaptive Multi-factor Authentication (MFA): Adaptive MFA enables an enterprise to enforce risk-aware and strong identity assurance controls within the organization.
Single Sign-On (SSO): SSO is the ability to use a single secure identity to access all applications and resources within an organization. CyberArk Identity enables SSO for all types of users (workforce, partners, and consumers) to all types of workstations, systems, VPNs, and applications both in the cloud and on-premises.
Secure Web Sessions: Secure Web Sessions records, audits and protects end-user activity within designated web applications. The solution uses a browser extension on an end-user’s endpoint to monitor and segregate web apps that are accessed through SSO and deemed sensitive by business application owners, enterprise IT and security administrators.
Workforce Password Management: CyberArk Workforce Password Management is an enterprise-focused password manager providing a user-friendly solution to store data from business applications -like website URLs, usernames, passwords and notes – in a centralized vault and securely share it with other users in the organization.
Application Gateway: With the CyberArk Identity Application Gateway service, customers can enable secure remote access and expand SSO benefits to on-premises web apps — like SharePoint and SAP — without the complexity of installing and maintaining VPNs.
Identity Lifecycle Management: This module enables CyberArk Identity customers to automate the joiner, mover, and leaver processes within the organization. This automation is critical to ensure that privileges don’t accumulate, and a user’s access is turned off as soon as the individual changes roles or leaves the organization.
Directory Services: Allows customers to use identity where they control it. In other words, the company do not force the company’s customers to synchronize their on-premises Active Directory implementation with the company’s cloud. The company’s cloud architecture can work seamlessly with any existing directory, such as Active Directory, LDAP-based directories, and other federated directories. CyberArk Identity also provides its own highly scalable and flexible directory for customers who choose to use it.
Customer Identity offers authentication and authorization services, MFA, directory, and user management to enable organizations to provide customers and partners with easy and secure access to websites and applications.
In alignment with the company’s Identity Security strategy, the company sells packaged offerings that align with the requirements of workforce users, privileged users, and external vendors. The workforce user offering includes credential vaulting and sharing, Adaptive MFA, and SSO. The privileged users offering includes full credential management, session management, and Remote Access. The external vendor offering aligns to the capabilities detailed above for Vendor Privileged Access Manager.
Secrets Management
The company’s capabilities in the area of Secrets Management are focused on securing secrets used by machine identities, such as applications, scripts, containers, DevOps tools, and third-party security solutions. Secrets Manager enables organizations to avoid the need to store secrets within applications and instead allows them to easily and securely access the required credentials from the CyberArk Vault. Secrets Manager supports traditional applications with its Credential Providers and dynamic applications with Conjur.
Secrets Manager Credential Providers: Credential Providers can be used to provide and manage the credentials used by third-party solutions, such as security tools, RPA, and IT management software, and also supports internally developed applications built on traditional monolithic application architectures. Credential Providers works with CyberArk’s on-premises and SaaS based solutions.
Conjur Secrets Manager and Conjur Cloud Secrets Manager: For cloud-native applications built using DevOps methodologies, Conjur Enterprise and Conjur Cloud provide a secrets management solution tailored specifically to the unique requirements of these environments delivered either on-premises or in the cloud. The company also provides an open-source version to better meet the needs of the developer community.
AWS Secrets Hub: For organizations developing in AWS Secrets Manager, Secrets Hub centrally manages and rotates secrets in CyberArk’s Conjur while enabling developers to continue to develop in the native AWS environment.
Cloud Privilege Security
Cloud Entitlements Manager. CyberArk Cloud Entitlements Manager is a SaaS solution that reduces risks that arise from excessive privileges by implementing Least Privilege across cloud environments. From a centralized dashboard, Cloud Entitlements Manager provides visibility and control of permissions across an organization’s cloud landscape. Within this single display, Cloud Entitlements Manager offers automatically deployable remediations based on the principle of Least Privilege, to help organizations strategically remove excessive permissions without disrupting cloud operations.
Identity Management
The company’s capabilities in Identity Management include Lifecycle Management, Identity Flows, Identity Compliance and directory services. The company’s Identity Management solutions are designed to provide a single view of who has access to what, ensuring that the right access is granted for the right amount of time to the right people. CyberArk Lifecycle Management streamlines provisioning and management of entitlements throughout a user’s employment, including approval workflows, access certifications and providing and revoking access. CyberArk Identity Flows is a no-code identity management workflow solution that reduces complexity and manual tasks to easily create workflows and automate business processes. CyberArk Identity Compliance enables customers to discover, certify, remediate and audit access, ensuring that an organization can implement Zero Trust across the enterprise.
Technology
The company’s portfolio provides a complete and flexible set of Identity Security capabilities that leverage the following core technologies:
Identity Security Platform Shared Services: The company’s Shared Services enable operational efficiencies, leveraging a single admin portal with unified audit, consistent authentication and authorization for all identities and Identity Security intelligence. The platform allows for secure role-based access to CyberArk SaaS through a single user interface to improve operational efficiencies for CyberArk solutions.
Secure Digital Vault Technology: The company’s proprietary Digital Vault technology provides a highly secure, isolated environment, independent of other software, and is engineered with multiple layers of security. The company’s on-premises and SaaS PAM solutions use the highly secured Digital Vault to safely store, audit and manage passwords, privileged credentials, policy information and privileged access session data.
Privileged Session Recording and Controls: The company’s privileged session recording and control mechanisms provide the ability to isolate an organization’s IT systems from end-user desktops, while monitoring and auditing privileged session activities. The architecture blocks direct communication between an end-user’s desktop and a target system, thus preventing potential malware on the desktop from infiltrating the target system. This architecture further ensures that privileged credentials will remain protected and will not be exposed to the end-user or reach the desktop. CyberArk session monitoring solutions support native connectivity, whether from browser, native RDP or SSH tools, and via the CLI (Command Line Interface). Risk scoring can be applied to each recorded session, automating the review of all privileged sessions and enabling auditors to prioritize and deprioritize workloads based on risk.
Secure Remote Access: The cloud-based, multifactor authentication provided with Remote Access leverages the biometric capabilities from smartphones which in turn allows authorized remote vendors simple just-in-time secure privileged access. Once authenticated, all privileged sessions are automatically recorded for full audit and monitored in real-time.
Strong Application Authentication and Credential Management: The Secrets Manager architecture allows an organization to eliminate hard-coded application credentials, such as passwords and encryption keys, from applications and scripts. The company’s secure, proprietary technology permits authentication of an application during run-time, based on any combination of the application’s signature, executable path or IP address, and operating system user. Following application authentication, the authenticated application uses a secure application programming interface (API), to request privileged account credentials during run-time and, based on the application permissions in Privileged Access Manager, up-to-date credentials are provided to the application.
Strong Endpoint Security: The company’s endpoint agent technology provides policy-based privilege management, application control and credential theft protection capabilities. The agent detects privileged commands, and application installation or invocation on the endpoint to validate whether it is permissible in accordance with the organization’s security policy, otherwise blocking the operation or allowing it to run in a restricted mode. Having users operate in a least privilege mode together with the company’s agent-based technology effectively reduces the attack surface that attackers or malware can exploit. The solution leverages third-party threat and reputation information to further strengthen controls and block bad or malicious applications based on such security intelligence.
Adaptive Multi-factor Authentication: The company’s Adaptive Multi-factor Authentication (MFA) enforces risk-aware and strong identity assurance controls within an organization. These controls include a broad range of built-in authentication factors, such as passwordless authenticators like Windows Hello and Apple TouchID, high assurance authenticators like USB security keys, and the company’s patented Zero Sign-on certificate-based authentication.
Single Sign-on: The company’s Single Sign-on (SSO) solution facilitates the secure access to many different applications, systems, and resources while only requiring a single authentication. The company’s SSO solution offers a modern identity provider supporting popular SSO protocols to any system or app that supports SAML, WS-Fed, OIDC and OAuth2, as well as an extensive application catalog with out-of-the-box integration for thousands of applications.
Customers
As of December 31, 2022, the company had more than 8,000 customers, including more than 55% of Fortune 500 companies and more than 35% of Global 2000 companies. The company’s customers include leading organizations in a diverse set of industries, including financial services, manufacturing, insurance, healthcare, energy and utilities, transportation, retail, technology and telecommunications, as well as government agencies.
Marketing
The company executes its strategy by leveraging a combination of internal marketing professionals and a network of channel partners to communicate the company’s value proposition and differentiation for the company’s products, generating qualified leads for the company’s sales force and channel partners. The company’s marketing efforts include global inbound and outbound demand generation campaigns, account-based marketing, public relations in multiple geographies and the publication of a broad array of content made available through the company’s website.
Sales
The company maintains a highly trained sales force that is responsible for developing and closing new business, the management of relationships with the company’s channel partners and the support and expansion of relationships with existing customers. The company’s sales organization is organized by geographic regions, consisting of the Americas, EMEA, the Asia Pacific and Japan. As of December 31, 2022, the company’s global network of channel partners consisted of more than 450 resellers, distributors, and managed service providers. The company’s channel partners generally complement its sales efforts by helping identify potential sales targets, maintaining relationships with certain customers, introducing new products to existing customers, and offering post-sale professional services and technical support.
In 2022, the company generated approximately 24% of its revenues from direct sales from the company’s field offices located throughout the world. The company works with many global systems integration partners and several leading regional security value added resellers, such as Optiv Security Inc., Merlin International, Computacenter United States Inc., Netpoleon, SHI, M.Tech and GuidePoint Security. Further, the company works with advisory firms, such as Deloitte, PricewaterhouseCoopers LLP, and KPMG in co-marketing and co-delivery of the company’s solutions and providing implementation services to the company’s customers.
Through CyberArk’s C3 Alliance, the company’s global technology partner program, the company bring together enterprise software, IT, Security, and cloud providers to build on the power of Identity Security to better protect customers from cyber threats. The company’s CyberArk Marketplace provides a trusted platform for customers to easily find and deploy integrations from the C3 Alliance, partners, and community members.
The company’s sales cycle varies by size of the customer, the number of products purchased and the complexity of the customer’s IT infrastructure, ranging from several weeks for incremental sales to existing customers to several months for large deployments. The company also typically experiences seasonality in the company’s sales, particularly demonstrated by increased sales in the last month of a quarter and the last quarter of the year (year ended December 2022). To support the company’s broadly dispersed global channel partners and customer base in the company’s hybrid model, the company had sales personnel in 41 countries as of December 31, 2022. The company plans to continue investing in the company’s sales organization to support both the growth of the company’s channel partners and the company’s direct sales organization.
Professional and Support Services
Maintenance and Support
The company’s maintenance and support program provides all customers who purchase maintenance and support in conjunction with their perpetual licenses, and customers who purchase self-hosted and SaaS subscriptions, the right to software bug repairs, the latest software enhancements, and updates on an if-and-when available basis during the maintenance period or subscription term, and access to the company’s technical support services.
The company’s technical support services are provided to perpetual and subscription customers via the company’s online support center, which enables customers to submit new support queries and monitor the status of open and past queries. The company’s online support system also provides customers with access to the company’s CyberArk Knowledge Base, an online user-driven information repository that provides customers the ability to address their own queries. Additionally, the company offers email and telephone support during business hours to customers that purchase a standard support package and 24/7 availability to customers that purchase the company’s 24/7 support or subscription package.
The company’s global customer support organization has expertise in the company’s software and how it interacts with complex IT environments. The company typically provides all levels of support directly to the company’s customers.
Professional Services
The company’s products are designed to allow for online trials, or to allow customers to download, install and deploy them on their own or with training and professional assistance. The company’s solutions are highly configurable, and many customers will select either one of the company’s many trained channel partners or the company’s CyberArk Security Services team to provide expert professional services. The company’s Security Services team can be contracted to assist customers in planning, installing, and configuring the company’s solution to meet the needs of their security and IT environment, and provide technical account management services. The company’s Security Services team provides ongoing consulting services regarding best practices for achieving Identity Security, and recommended ways to implement the company’s solutions to meet specific customer requirements. Additionally, they share best practices associated with Identity Security to educate customers and partners on such best practices through virtual classroom, live face-to-face, or self-paced classes. The company also has Red Team services, which specialize in adversary simulations to test customers’ and prospects’ cloud and hybrid environments, DevOps pipelines and processes to help make their environment more secure.
In 2021, the company introduced new professional services solutions aimed at delivering faster time to value and helping customers streamline the deployment of certain CyberArk SaaS products, while providing a resource to help to implement a phased approach to a Privileged Access Management program, from planning, to pilot, to production. In addition, in 2022, the company expanded its professional services packages by offering outcome-based services that corresponded with each of the company’s SaaS solutions.
Research and Development
The company’s research and development expenses were $190.3 million in 2022.
Intellectual Property
As of December 31, 2022, the company had 130 issued patents in the U.S., and 49 pending U.S. patent applications. The company also had 59 issued patents and 20 applications pending for examination in non-U.S. jurisdictions, all of which are counterparts of the company’s U.S. patent applications.
The inventions for which the company has sought patent protection relate to elements of the company’s products and technology. The following list of products identifies some of those with patent-protected features, but other products may also be protected by one or more patents: Privileged Access Security (PAS) solutions, including Privileged Access Manager, Vendor Privileged Access Manager, Privileged Session Manager (PSM), Enterprise Password Vault (EPV), Privilege Cloud, CyberArk DNA (Discovery and Audit), Privileged Threat Analytics (PTA), Endpoint Privilege Manager (EPM), Sensitive Information Management (SIM) and Cloud Entitlements Manager (CEM); Secret Management Solutions, including Conjur Secrets Manager Enterprise, Conjur Secrets Manager Open Source, Credential Providers, Secretless and Secretless Broker; and Access Management Solutions, including CyberArk Identity, Workforce Identity, Customer Identity and Secure Web Sessions.
Competition
Specifically, the company’s Identity Security Platform competes across a variety of markets and competitors, including, but not limited to:
Privileged Access Management (PAM), including Endpoint Privilege Management, such as Delinea and BeyondTrust;
Identity and Access Management, such as Okta and Microsoft; and
Secrets Management, including broad DevOps solutions, such as Hashi Corporation.
History
CyberArk Software Ltd. was founded in 1999.

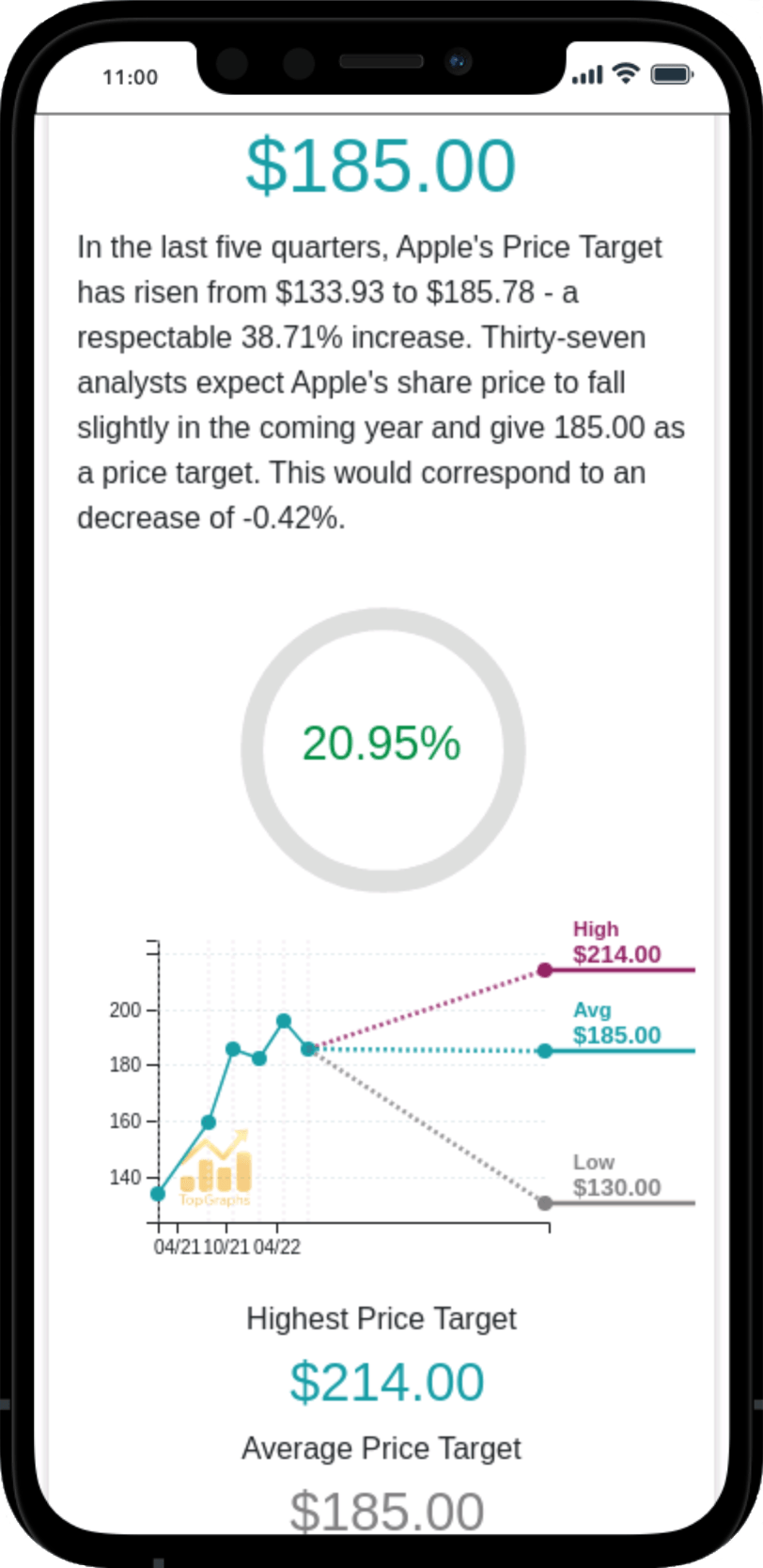
 Stock Value
Stock Value